“零信任”是最近在互联网上流行的安全术语之一, 但是它是什么意思,为什么安全或it审计团队应该开始关心这个术语? 传统上, 澳门赌场官方下载关心的是通过部署防火墙形成一个分层的防御边界, web proxies and other boundary isolation mechanisms to keep malicious actors out while expressing a certain level of inherent trust for the devices operating within the enterprise network interior. 这种传统的网络防御模式根本行不通 网络攻击增加600% 自COVID-19单独出现以来,通常取得了很大程度的成功. 由于物联网技术的发展,恶意行为者也有了更多的攻击途径, 云技术和针对用户的持续的网络钓鱼攻击. The cost of continuing to protect the enterprise’s critical assets and data using the traditional security approach is becoming increasingly ineffective with the average security breach toward the end of 2021 给澳门赌场官方下载造成的损失高达4美元.2400万年.
这篇博文将概述零信任安全模型,以及如何在整个澳门赌场官方下载中迭代地建立零信任(请参阅相关的ISACA白皮书). The blog post will also lay out some potential audit or consultation approaches audit departments can adopt to strengthen their position as “trusted advisors” within the enterprise. 零信任并不寻求完全取代当前的网络保护模型,甚至不寻求改变基础设施, 而是增强它们以增强网络保护. Readers may take the opportunity to simply increase their knowledge on this topic or begin building assessment plans to determine readiness or the adequacy of controls needed to support this emerging model.
零信任生命周期
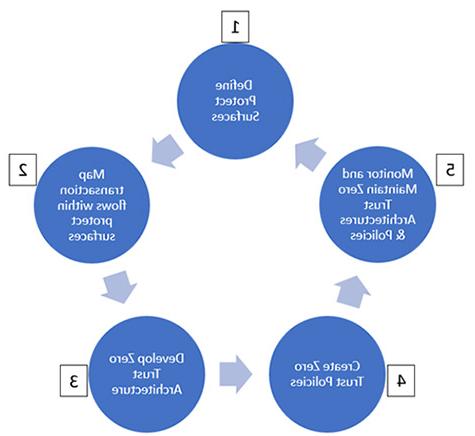
- 定义保护表面
The traditional security approach typically focuses efforts on defining and protecting a security perimeter around the enterprise network and attempting to distance sensitive data or vulnerable information systems from this perimeter. The remote workforce str等hes this traditional boundary into the user’s home network through the use of technologies like VPN and makes not only defining the enterprise network challenging, 但也使国防资源分配困难.
Zero Trust通过明确定义和开发带有关键数据分组的“保护表面”来脱离这个模型, 应用程序, 资产, & 按实际使用量付费服务().- 数据应根据其对澳门赌场官方下载的相对重要性进行详尽的识别和分类, 客户, 和业务伙伴使用数据分类策略或标准.
- 应该评估应用程序,以确定它们存储的敏感数据的级别, transmit or process and the value of the application to the enterprise should it become unavailable or be held ransom by malicious actors.
- 资产(笔记本电脑、平板电脑、服务器、路由器等.)应详尽清点,并进一步评估是否包含在个别保护表面.
- 服务(DNS、E-mail、DHCP等.)应被识别和评估是否包含在保护表面.
- 映射事务流在保护表面
在定义了单独的保护表面之后, 应该努力确定数据如何, 应用程序, 资产和服务彼此交互. 这包括端口的确定, 协议, 网络流量基线, 网络上的源和目标位置. This mapping exercise will enable the enterprise to fine-tune and implement a custom degree of protection required for each protect zone without compromising usability, DAAS的性能和可用性.
此阶段的审计重点可能包括获取和检查与保护表面有关的网络图文件, whether relevant DAAS is accounted for within each diagram and if sufficient details are present depicting interaction between in scope DAAS. Further assurance activities may include assessing whether initial security policies defined in the previous steps have been modified or require additional controls following this review and if a routine review of the DAAs interdependencies is formally scheduled to identify changes and adjust security policy accordingly. - 开发零信任架构
Zero Trust is not simply about access control but also effectively leveraging a multitude of technologies such as deep packet inspection, 端点保护, 防止数据丢失, 网络过滤, 等.,只允许可信事务在网络上发生. 在澳门赌场官方下载保护表面和它们各自的DAAS相互依赖关系被确定之后, 根据澳门赌场官方下载独特的保护需求,可以形成实际的零信任体系结构. 澳门赌场官方下载s will typically seek to use a firewall or other network isolation mechanisms to separate protect surfaces from each other, 创建“micro-perimeters.“下一代防火墙由于其固有的能力是这一阶段的支柱 在OSI模型的所有七层提供网络过滤.
Audit focus at this stage may piggyback off the previous step to determine if the inclusion of specific security appliances or services listed above are readily associated to protect surfaces and properly situated on the network. Audit focus may also include determining if a well-architected review with appropriate technology and business executive sign-off has occurred to validate that the architecture meets business requirements. - 创建零信任策略
零信任策略的创建规定了“吉卜林方法”的使用。 确保授予主体(如用户或系统)的任何访问权限都是适当的. 这包括详尽地确定:- 应该允许谁访问澳门赌场官方下载DAAS?
- 哪些应用将被允许访问澳门赌场官方下载DAAS?
- 何时应该访问澳门赌场官方下载DAAS?
- 澳门赌场官方下载DAAS位于何处(物理上或逻辑上)?
- 为什么需要访问澳门赌场官方下载DAAS?
- 如何授予对澳门赌场官方下载DAAS的访问权限?
- 监控和维护零信任架构
Monitoring Zero Trust requires frequent logs reviews and inspection of artifacts produced by security appliances and end-point protection solutions. 随着时间的推移, 澳门赌场官方下载应该寻求基线并确定网络上关于资产通信的正常行为, 数据交易量和用户活动. 传入模型以进行评估和调优的数据越多, 更好的, as the monitoring activity and fine-tuning allow the protection applied to individual protect surfaces to become increasingly resilient.
这一阶段的审计重点应包括确定管理层是否采用正式的基准, 记录审查和保护地面改进活动. Audit focus may also include whether planned changes to security policies are resulting from these reviews and refinements then being implemented as directed.
零信任并不寻求取代现有的基础设施,也不会让澳门赌场官方下载承担巨大的成本来实现其利益. Zero Trust’s iterative nature also allows the organization to adopt the model slowly through the development of a single protect surface while model efficiencies and benefits become apparent. Internal auditors may assist the enterprise in this journey by educating themselves on the benefits of Zero Trust architecture and determining the extent to which they are following successful strategies for the adoption of this emerging security architecture model.
